Trade news
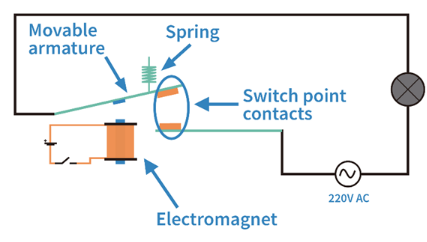
Security routers make OT networks secure
Key word:
Popular categories
- Week of hot material
- Material in short supply seckilling
| model | brand | Quote |
|---|---|---|
| BD71847AMWV-E2 | ROHM Semiconductor | |
| TL431ACLPR | Texas Instruments | |
| RB751G-40T2R | ROHM Semiconductor | |
| CDZVT2R20B | ROHM Semiconductor | |
| MC33074DR2G | onsemi |
| model | brand | To snap up |
|---|---|---|
| ESR03EZPJ151 | ROHM Semiconductor | |
| TPS63050YFFR | Texas Instruments | |
| IPZ40N04S5L4R8ATMA1 | Infineon Technologies | |
| BP3621 | ROHM Semiconductor | |
| BU33JA2MNVX-CTL | ROHM Semiconductor | |
| STM32F429IGT6 | STMicroelectronics |
Hot labels
ROHM
IC
Averlogic
Intel
Samsung
IoT
AI
Sensor
Chip
Information leaderboard
- Week of ranking
- Month ranking
About us
Qr code of ameya360 official account
Identify TWO-DIMENSIONAL code, you can pay attention to


AMEYA360 mall (www.ameya360.com) was launched in 2011. Now there are more than 3,500 high-quality suppliers, including 6 million product model data, and more than 1 million component stocks for purchase. Products cover MCU+ memory + power chip +IGBT+MOS tube + op amp + RF Bluetooth + sensor + resistor capacitance inductor + connector and other fields. main business of platform covers spot sales of electronic components, BOM distribution and product supporting materials, providing one-stop purchasing and sales services for our customers.